This list of Malware types only scratches the surface as malware is constantly being developed and unleashed by those trying to gain access to your computer for monetary gain. The list of Malware types focuses on the most common and the general categories of infection
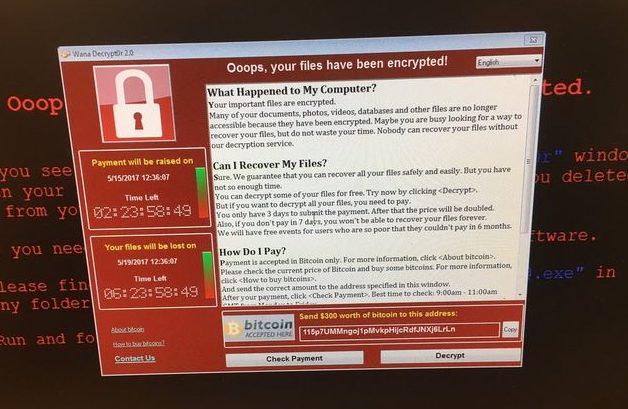
Ransomware
If you see this screen that warns you that you have been locked out of your computer until you pay for your files to be unlocked. Your system is severely infected with a form of Malware called Ransomware. Even if you pay to unlock the system, the system is unlocked, but you are not free of it locking you out again. The request for money, usually in the hundreds of dollars or for bitcoins is completely fake.
Browser Hijacker
When your homepage changes to one that looks like those in the images inserted next, you may have been infected with one form or another of a Browser Hijacker. This dangerous Malware will redirect your normal search activity and give you the results the developers want you to see. Its intention is to make money off your web surfing. Using this homepage and not removing the Malware lets the source developers capture your surfing interests. This is especially dangerous when banking or shopping online. These homepages can look harmless, but in every case they allow other more infectious.
Virus
A virus is a contagious program or code that attaches itself to another piece of software, and then reproduces itself when that software is run. Most often this is spread by sharing software or files between computers.
Worm
A program that replicates itself and destroys data and files on the computer. Worms work to eat the system operating files and data files until the drive is empty.
Trojans and backdoors
The most dangerous Malware. Trojans are written with the purpose of discovering your financial information, taking over your computers system resources, and in larger systems creating a denial-of-service attack Denial-of-service attack: an attempt to make a machine or network resource unavailable to those attempting to reach it. Example: AOL, Yahoo or your business network becoming unavailable.
Backdoors are much the same as Trojans or worms, except that they open a backdoor onto a computer, providing a network connection for hackers or other Malware to enter or for viruses or SPAM to be sent.
Adware and Spyware
The least dangerous and most lucrative Malware. Adware displays ads on your computer. Spyware is software that spies on you, tracking your internet activities in order to send advertising (Adware) back to your system.
Keyloggers
Records everything you type on your PC in order to glean your log-in names, passwords, and other sensitive information, and send it on to the source of the keylogging program. Many times keyloggers are used by corporations and parents to acquire computer usage information.
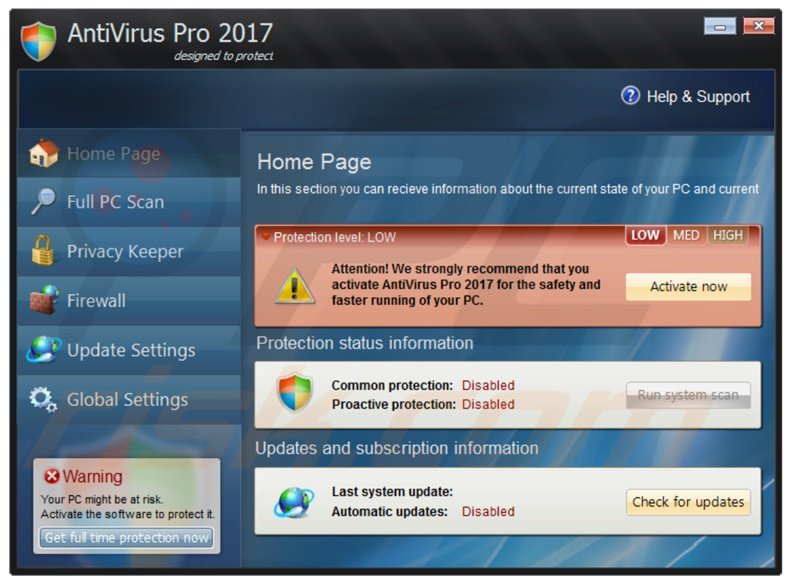
Rogue security software
This one deceives or misleads users. It pretends to be a genuine and reliable program to remove Malware infections, but all the while it is the Malware. Often it will turn off the real Anti-Virus software.
Need help? Computer infected with malware?
If you’re experiencing any of the above symptoms get in touch with Fixed Locally, our Virus Removal and Malware Removal services provide a reliable way to clean up your computer or laptop from virus and malware infections.

